Run Pomerium Core With Docker
Run Pomerium Core with Docker containers in under 5 minutes.
The Core quickstart uses Pomerium's Hosted Authenticate Service, but you can also configure a self-hosted authenticate service to integrate with Pomerium.
Prerequisites
Docker and Docker Compose
Configure Pomerium
Create a config.yaml file in the root of your project.
Add the configuration below to config.yaml:
# See detailed configuration settings: https://www.pomerium.com/docs/reference/
#####################################################################
# If self-hosting, use the localhost authenticate service URL below #
# and remove the hosted URL. #
#####################################################################
# authenticate_service_url: https://authenticate.localhost.pomerium.io
authenticate_service_url: https://authenticate.pomerium.app
####################################################################################
# If self-hosting, you must configure an identity provider. #
# See identity provider settings: https://www.pomerium.com/docs/identity-providers/#
####################################################################################
# https://pomerium.com/reference/#routes
routes:
- from: https://verify.localhost.pomerium.io
to: http://verify:8000
policy:
- allow:
or:
- email:
is: user@example.com
pass_identity_headers: true
Replace user@example.com with your email address.
Configure Docker
Create a docker-compose.yaml file in the root of your project.
Add the configuration below to docker-compose.yaml:
version: "3"
services:
pomerium:
image: cr.pomerium.com/pomerium/pomerium:latest
volumes:
## Mount your config file: https://www.pomerium.com/docs/reference/
- ./config.yaml:/pomerium/config.yaml:ro
ports:
- 443:443
## https://verify.localhost.pomerium.io --> Pomerium --> http://verify
verify:
image: cr.pomerium.com/pomerium/verify:latest
expose:
- 8000
Run Docker Compose
docker compose up
Access the verify route you built in your policy: https://verify.localhost.pomerium.io
If you get a self-signed certificate warning, see Handle Self-Signed Certificate Warning to bypass it.
You should be redirected to the verify service. You'll see a page like this:
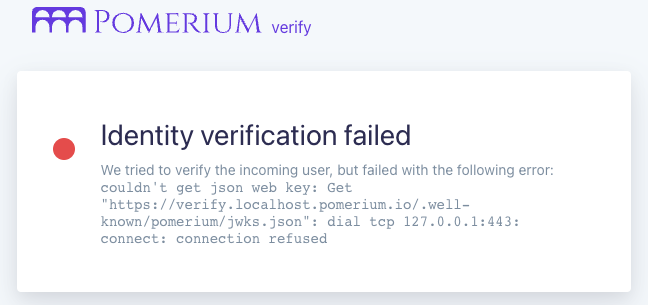
Although identity verification failed, you successfully integrated Pomerium with the upstream verify service.
Because this guide doesn't include a signing key in the configuration, identity verification will fail.
See Identity Verification for more information on how Pomerium can use JWTs for authentication.
Next Steps
If you want to try Enterprise, check out the Enterprise with Docker quickstart.
If you want to try connecting Pomerium with other services, see some of our Guides.
Did you finish this quickstart guide? We'd love to hear what you think. Get in touch with us on our Discuss forum, message us on Twitter, LinkedIn, or check out our Community page.
This is a test environment! If you followed all the steps in this doc your Pomerium environment is not using trusted certificates. Remember to use a valid certificate solution before moving this configuration to a production environment. See Certificates for more information.